What is SSL and TLS? and Security Fix

TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols used to secure communication on the internet. Both provide encryption of information during data transfer, thus providing security services such as confidentiality, integrity and authentication.
SSL: (Secure Sockets Layer):
SSL was developed by Netscape Communications and first published in 1995. It was the first protocol used to encrypt and secure communications on the Internet. The main goal of SSL is to ensure that communication between client and server is confidential. SSL forms the basis of the HTTPS (HTTP Secure) protocol commonly used on websites. It is used in communication between browsers and servers, allowing websites to provide a secure connection to their visitors. However, due to the emergence of SSL's security vulnerabilities and its inability to keep up with developing technology, it was replaced by TLS over time.
TLS: (Transport Layer Security):
TLS was developed to replace SSL and was released in 1999. TLS is an improved and vulnerable version of SSL. The process, which started with the transition from SSL 3.0 to TLS 1.0, continues today with TLS 1.2 and TLS 1.3 versions. TLS makes communication on the internet more secure. This protocol increases the security of data by using advanced encryption algorithms. Additionally, it provides authentication and data integrity. Nowadays, TLS is more common to use because SSL has security vulnerabilities and is no longer supported. It allows a secure connection to be used in communication between browsers and servers.
How (TLS) Transport Layer Security Works?

- Handshake: A handshake process takes place between the client and the server that initiates the communication. In this process, parties share their certificates and generate encryption keys to authenticate each other. This step is a fundamental step to ensure the security of communication.
- Encryption and Authentication: After the handshake process, communication between the parties is encrypted and authenticated. This step ensures the security and confidentiality of the data.
- Data Transfer: Encrypted data is transmitted securely between parties. Data integrity is ensured, meaning it is verified that the data has not been modified or corrupted.
- Connection Termination: When communication is completed, the connection between the parties is terminated. This step ensures that the communication ends safely.
How (SSL) Secure Sockets Layer Works?
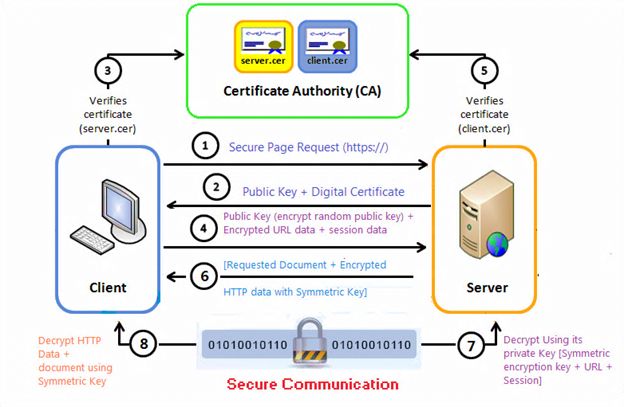
- Client Connection: The client (for example, a web browser) connects to the server and wants to establish a secure connection.
- Server Authentication: The server typically sends a digital certificate to the client. This certificate authenticates the server and proves that a secure connection has been established.
- Private Key Sharing: The server sends a private key to the client, which will be used to encrypt the connection. This key is used to securely transmit the symmetric encryption key that will be used to secure the connection.
- Generation of Symmetric Encryption Key: The client creates a symmetric encryption key for the connection using the private key sent by the server. This key is used to encrypt and decrypt communications.
- Encryption and Transmission of Data: All data between the client and the server is now encrypted and transmitted securely using the generated symmetric encryption key.
- Termination of Connection: When communication is completed, the connection between the client and server is terminated and the encryption keys are deleted.
These steps constitute the basic working principle of SSL. In this way, communication on the internet is made secure and data is transmitted securely.
TLS ⚔️ SSL

People continue to use SSL when referring to TLS even now, but SSL is no longer supported by most web browsers as this protocol has been considered insecure for many years. The latest version of SSL, SSL 3.0, has been deprecated since 2015.
The most common uses of SSL and TLS:
- Secure Web Communication (HTTPS): SSL and TLS are used in the HTTPS protocol to encrypt communication between web browsers and servers. In this way, users can communicate with websites securely.
- Email Security: SSL and TLS are used to encrypt communications between email servers. In this way, e-mail traffic is protected from surveillance by malicious individuals or institutions.
- VPN Connections: Some VPN services use SSL and TLS to encrypt and securely transmit users' internet traffic.
- Secure File Transfer: SSL and TLS are used to encrypt file transfers through file transfer protocols (FTP, SFTP, SCP, etc.)
- Secure API Communication: SSL and TLS are used to encrypt communication between web services and APIs, ensuring data security.
The most common use of SSL/TLS that you can find on the internet is that it is applied on top of the HTTP (Hypertext Transfer Protocol) protocol and creates an extension known as HTTPS (Secure Hypertext Transfer Protocol). Therefore, any website that uses HTTPS also uses SSL/TLS encryption on a daily basis.
Difference Between HTTP and HTTP(S)
HTTP, which stands for Hyper Text Transfer Protocol, is the protocol used to view web pages. HTTPS stands for Secure Hyper Text Transfer Protocol. So it is Http with security feature.
Differences Between SSL and TLS in Summary:
- SSL Version History: SSL has been replaced by TLS. SSL has versions 1.0, 2.0 and 3.0.
- TLS Version History: TLS is the upgraded version of SSL, available in versions 1.0, 1.1, 1.2 and 1.3.
- Event: All SSL versions are deprecated. TLS versions 1.2 and 1.3 are actively used.
- Warning Messages: SSL has only two types of warning messages, and the warning messages are not encrypted. On the other hand, TLS alert messages are encrypted and are more diverse.
- Message Authentication: SSL uses MACs, while TLS uses HMACs.
- Cipher Suites: SSL supports legacy algorithms with known vulnerabilities, while TLS uses advanced encryption algorithms.
- Handshake: While the SSL handshake process is complex and slow, the TLS handshake has fewer steps and a faster connection.
How to Check the SSL/TLS Version

Check For Windows Server and Client:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
⚠️🔴Insecure SSL/TLS Versions:
> SSL 2.0
> SSL 3.0
> TLS 1.0
> TLS 1.1
✅✅✅Secure SSL/TLS Versions:
> TLS 1.2
> TLS 1.3
IIS Crypto Tool: https://www.nartac.com/Products/IISCrypto
Check For ssllabs: https://www.ssllabs.com/ssltest
REG Dir Server and Client:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server\Server
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client
Enable✅ Registry Configuration:
> Protocols
> SSL 2.0
> SSL 3.0
> TLS 1.0
> TLS 1.1
✔️✅ > TLS 1.2 ***
> Server
:DisabledByDefault (0)
:Enabled (1)
> Client
:DisabledByDefault (0)
:Enabled (1)
> TLS 1.3
Check For Linux Server and Client:
Apache:
To turn off SSL v3.0 on Apache;
SSLProtocol All -SSLv2 -SSLv3
Nginx:
For both TLS version 1.2 and 1.3 use the following in nginx config file:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
⚠️Note: TLS 1.3 is only supported in Windows Server 2022 and later.
Security Fix All Version REG File: Year 2024
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
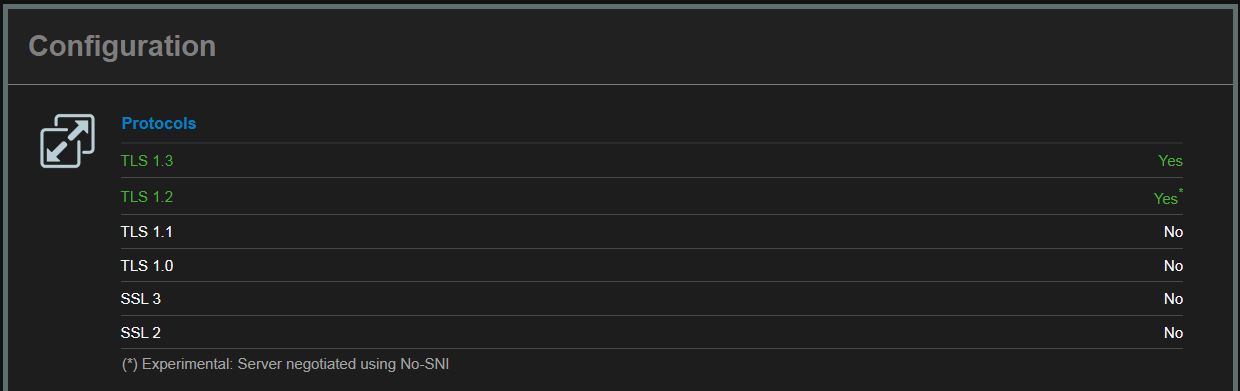
Result:

Written by theguler with love in Turkey 💖